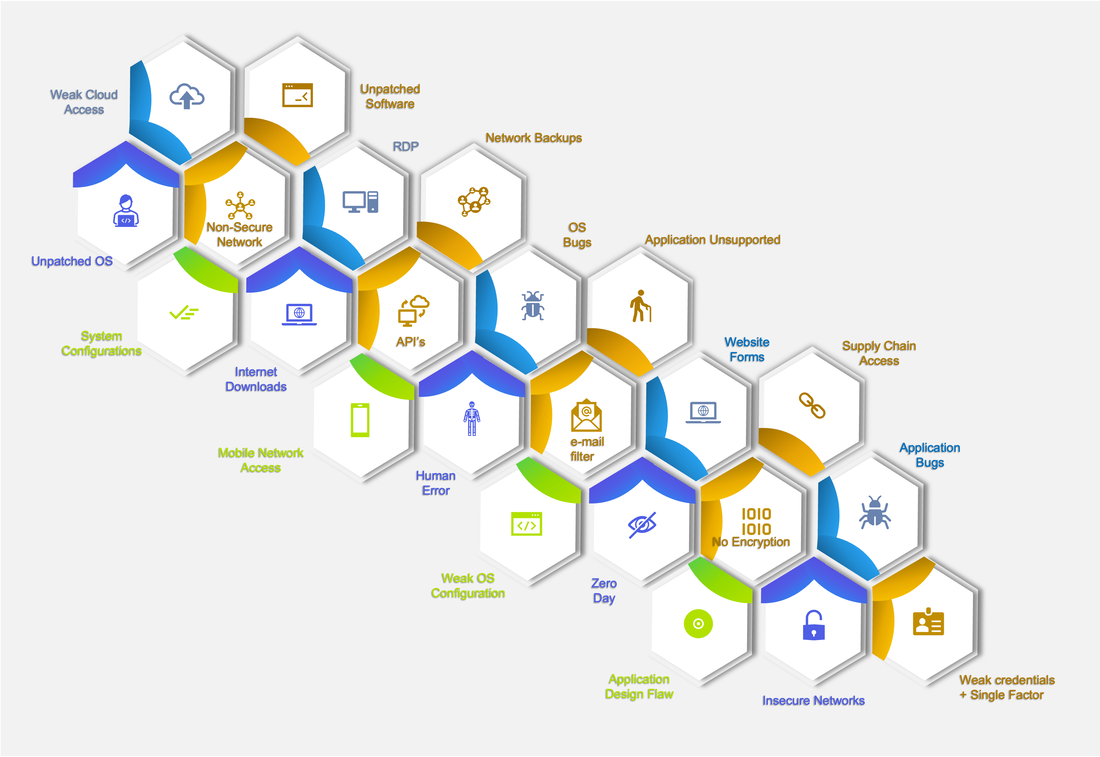
What are vulnerabilities and why should we careA vulnerability is a weakness in an IT system that can be exploited by an attacker to deliver a successful attack. They can occur through flaws, features or user error, and attackers will look to exploit any of them, often combining one or more, to achieve their end goal. A vulnerability, which has at least one definite attack vector is an exploitable vulnerability. Attackers will, for obvious reasons, want to target weaknesses in the system or network that are exploitable. Of course, vulnerability is not something that anyone will want to have, but what you should be more worried about is it being exploitable.There are cases when something that is vulnerable is not really exploitable. The reasons could be:
|
Shape Divider - Style triangle_asymmetrical